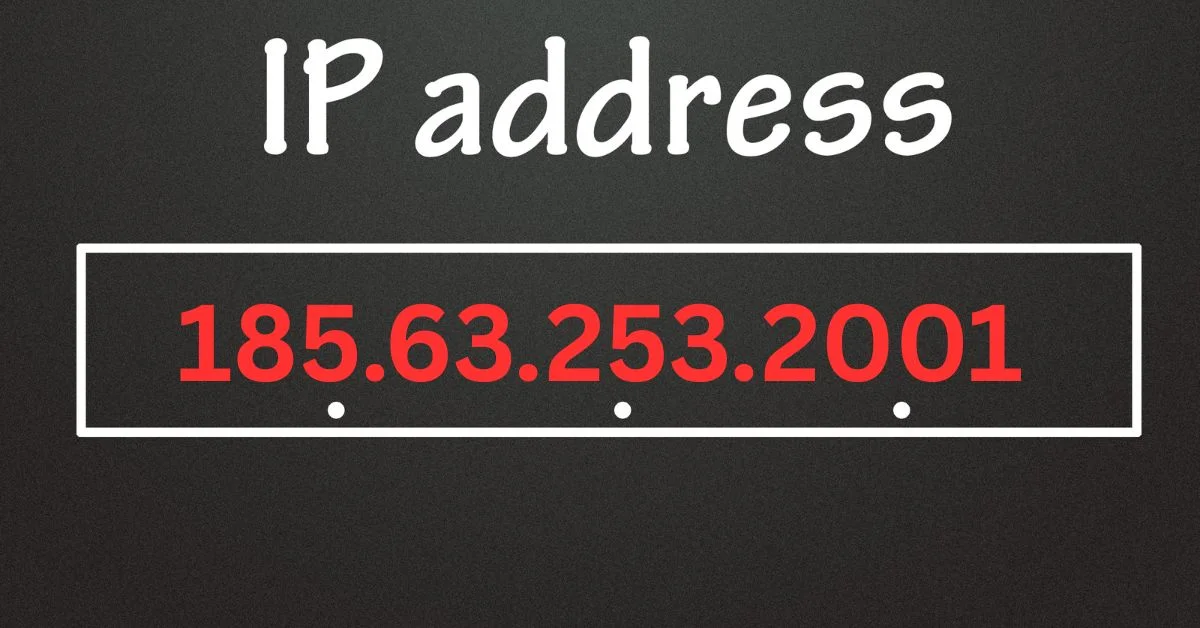
An IP address is a building block of the internet. An IP address is a unique identifier that allows any device to communicate with any other device on a local or global network. Strings like 185.63.253.2001 do pop up every once in a while, and they make you wonder what they mean and how they relate to networking and cybersecurity.
This article delves into the circumstances around the address 185.63.253.2001, explaining its structure, purpose, and methods for determining its validity or malevolence. We will cover key points such as IP standards, network protocols, and the function of addresses in digital infrastructure and system security as we go along.
What Is an IP Address?
An IP address (Internet Protocol address) is a unique string of numbers used to identify devices on a network. There are two main versions:
- IPv4: Uses a 32-bit address space, represented by four decimal numbers (e.g., 192.168.0.1).
- IPv6: Uses a 128-bit address space, written in hexadecimal (e.g., 2001:0db8:85a3::8a2e:0370:7334).
Every website, mobile device, router, or smart appliance that connects to the internet has an IP address. It facilitates data routing and identity verification.
Decoding 185.63.253.2001: Is It Valid?
At first glance, 185.63.253.2001 appears to be an IPv4 address. However, there’s a catch.
IPv4 addresses must consist of four decimal numbers, each ranging from 0 to 255. So:
- 185: ✅ valid
- 63: ✅ valid
- 253: ✅ valid
- 2001: ❌ Invalid (exceeds the 255 max)
IPv4 vs IPv6: Understanding the Basics
IPv4 Format:
- Example: 185.63.253.201
- 4 octets (e.g., A.B.C.D format)
- Each number between 0–255
- Total combinations: ~4.3 billion
IPv6 Format:
- Example: 2001:0db8:85a3:0000:0000:8a2e:0370:7334
- 8 groups of hexadecimal numbers
- More than 340 undecillion combinations
IPv6 addresses were introduced to solve the exhaustion of IPv4 space.
Common Uses and Misuses of IP Addresses
Legitimate Uses:
- Web browsing (resolving domains to IP addresses)
- Secure communications (VPN routing)
- Email delivery (SMTP relies on sender IP validation)
- Device identification in LANs
Misuses:
- IP Spoofing: Masking malicious activities
- DDoS Attacks: Launching traffic floods from multiple IPs
- Phishing or Redirection: Using malformed IPs to trick users
An address like 185.63.253.2001 could be misused in such deceptive practices.
Table: IP Address Classes and Ranges
| Class | Range | Purpose |
|---|---|---|
| Class A | 1.0.0.0 to 126.255.255.255 | Large networks |
| Class B | 128.0.0.0 to 191.255.255.255 | Medium-sized networks |
| Class C | 192.0.0.0 to 223.255.255.255 | Small networks |
| Class D | 224.0.0.0 to 239.255.255.255 | Multicast |
| Class E | 240.0.0.0 to 255.255.255.255 | Reserved (research) |
IP Reputation and Threat Detection
Cybersecurity platforms maintain IP reputation databases to identify harmful or suspicious activity. If a malformed IP like 185.63.253.2001 shows up:
- It may be flagged in server logs
- Could be part of a botnet scanning activity
- Might be an input in honeypot networks (used to trap bad actors)
Tools such as VirusTotal, AbuseIPDB, and Shodan can analyze suspicious IP addresses.

Cybersecurity Tips for IP Monitoring
If you’re a website admin, developer, or concerned user, here are key tips:
1. Validate IP Inputs
Always sanitize and validate IP address formats on forms and APIs.
2. Monitor Server Logs
Scan logs for unusual or malformed IP patterns like 185.63.253.2001.
3. Use Firewalls and IDS/IPS
Implement systems that detect suspicious traffic based on IP reputation.
4. Geo-IP Filtering
Block or restrict access based on geographic risk levels.
5. Whitelist Trusted IPs
Allow only approved addresses to access sensitive systems.
Conclusion
You shouldn’t disregard 185.63.253.2001 just because it shows up in logs or traffic statistics; it isn’t a genuine IP address. A security breach attempt, a misconfiguration, or a mistake might be the cause. Organisations and individuals may better safeguard themselves when they have a firm grasp of IP addresses, how they function, and the forms in which they appear.
Keep your wits about you. When in doubt, explore, and use tools to validate formats. Keep your IP monitoring procedures current and strong if you are in charge of digital infrastructure.
FAQs
Q1: Is 185.63.253.2001 a real IP address?
No, it is not a valid IPv4 address because 2001 exceeds the maximum value (255) allowed in any octet.
Q2: Can 185.63.253.2001 be used for routing or hosting?
No. Network devices will reject it as invalid input.
Q3: Why might such an address appear in logs?
It could be a typographical error, malicious obfuscation, or malformed input from automated bots.
Q4: How do I check if an IP is dangerous?
Use services like AbuseIPDB, IPVoid, or VirusTotal to assess IP reputation.
Q5: What should I do if I suspect an attack from an invalid IP?
Check logs, update firewall rules, and consult your IT or cybersecurity team to take immediate action.
For more information, click here.